Keywords: intrusion detection system, classification algorithm, and metaheuristic algorithm.
Ze-Hong Chen1, a , Yi-Lin Chen1,b, Wei-Yan Chang1,c , and Chun-Wei Tsai2,d*
1Computer Science and Engineering, National Chung Hsing University, Taiwan, R.O.C.
2Computer Science and Engineering, National Sun Yat-sen University, Taiwan, R.O.C.
a This email address is being protected from spambots. You need JavaScript enabled to view it., b This email address is being protected from spambots. You need JavaScript enabled to view it., c This email address is being protected from spambots. You need JavaScript enabled to view it., d This email address is being protected from spambots. You need JavaScript enabled to view it.
Abstract
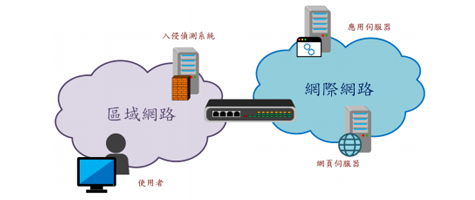
An intrusion detection system (IDS), which can be regarded as a subsystem of a network management system, plays the role of detecting and preventing abnormal network behaviors. With the advance of the Internet and the increase of the complexity of network architectures, many attack methods have been developed. However, most traditional intrusion detection systems are incapable of recognizing these attacks. Therefore, this study will present a hybrid classification algorithm for an intrusion detection system to improve its accuracy rate and reduce its computation time. The proposed algorithm integrates k-means (a clustering algorithm), support vector machine (a classification algorithm), and search economic (a metaheuristic algorithm). The experimental results show that the proposed hybrid algorithm provides a better accuracy rate in solving complex network attack classification problems.
References
- W. Stallings and L. Brown, Incident Response: Computer Security Principles and Practice, Prentice Hall Press, 2014.
- A. Mairh, D. Barik, K. Verma and D. Jena, “Honeypot in network security: A survey,” in Proceedings of the International Conference on Communication, Computing & Security, pp. 600-605, 2011. Google Scholar
- A. Patel, M. Taghavi, K. Bakhtiyari and J. C. Júnior, “An intrusion detection and prevention system in cloud computing: A systematic review,” Journal of Network and Computer Applications, vol. 36, no. 1, pp. 25-41, 2013. Google Scholar
- H. J. Liao, C. H. R. Lin, Y. C. Lin and K. Y. Tung, “Intrusion detection system: A comprehensive review,” Network and Computer Applications, vol. 36, no. 1, pp. 16-24, 2013. Google Scholar
- T. F. Lunt, “A survey of intrusion detection techniques,” Computers & Security, vol. 12, no. 4, pp. 405-418, 1993. Google Scholar
- I. Burguera, U. Zurutuza and S. Nadjm-Tehrani, “Crowdroid: Behavior-based malware detection system for android,” in Proceedings of the ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, pp. 15-26, 2011. Google Scholar
- C. Michel and L. Mé, “ADeLe: An Attack Description Language for Knowledge-Based Intrusion Detection,” in Proceedings of the IFIP International Information Security Conference, pp. 353-368, 2001. Google Scholar
- Z.H. Chen and C.W. Tsai, “An Effective Metaheuristic Algorithm for Intrusion Detection System,” in Proceedings of the IEEE International Conference on Smart Internet of Things, pp. 154-159, 2018. Google Scholar
- K. C. Lee and L. Mikhailov, “Intelligent intrusion detection system,” in Proceedings of the International IEEE Conference on Intelligent Systems, vol. 2, pp. 497-502, 2004. Google Scholar
- O. Depren, M. Topallar, E. Anarim, and M. K. Ciliz, “An intelligent intrusion detection system (IDS) for anomaly and misuse detection in computer networks,” Expert Systems with Applications, vol. 29, no. 4, pp. 713-722, 2005. Google Scholar
- G. Stein, B. Chen, A. S. Wu, and K. A. Hua, “Decision tree classifier for network intrusion detection with GA-based feature selection,” in Proceedings of the Annual Southeast Regional Conference, vol. 2, pp. 136-141, 2005. Google Scholar
- S. W. Lin, K. C. Ying, S. C. Chen, and Z. J. Lee, “Particle swarm optimization for parameter determination and feature selection of support vector machines,” Expert Systems with Applications, vol. 35, no. 4, pp. 1817-1824, 2008. Google Scholar
- F. Kuang, W. Xu, and S. Zhang, “A novel hybrid KPCA and SVM with GA model for intrusion detection,” Applied Soft Computing, vol. 18, pp. 178-184, 2014. Google Scholar
- C.W. Tsai, “Incremental Particle Swarm Optimization for Intrusion Detection," IET Networks, vol. 2, no.3, pp.124-130, 2013. Google Scholar
- A. Saied, R. E. Overill, and T. Radzik, “Detection of known and unknown DDOS attacks using artificial neural networks,” Neurocomputing, vol. 172, pp. 385-393, 2016. Google Scholar
- S. Kashef and H. Nezamabadi-pour, “An advanced ACO algorithm for feature subset selection,” Neurocomputing, vol. 147, pp. 271-279, 2015. Google Scholar
- R. A. R. Ashfaq, X. Z. Wang, J. Z. Huang, H. Abbas, and Y. L. He, “Fuzziness based semi-supervised learning approach for intrusion detection system,” Information Sciences, vol. 378, pp. 484-497, 2017. Google Scholar
- P. Casas, J. Mazel, and P. Owezarski, “Unsupervised network intrusion detection systems: Detecting the unknown without knowledge,” Computer Communications, vol. 35, pp. 772-783, 2012. Google Scholar
- C. W. Tsai, “An effective WSN deployment algorithm via search economics,” Computer Networks, vol. 101, pp. 178-191, 2016. Google Scholar
- C. Blum and A. Roli, “Metaheuristics in combinatorial optimization: Overview and conceptual comparison,” ACM Computing Surveys, vol. 35, no. 3, pp. 268-308, 2003.Google Scholar
- https://sites.google.com/a/uah.edu/tommy-morris-uah/ics-data-sets, Available: 2019/02/22.
- http://www.unb.ca/research/iscx/dataset/iscx-NSL-KDDdataset.html, Available: 2019/ 02/22.
- D. W. F. L. Vilela, E. W. T. Ferreira, A. A. Shinoda, N. V. de Souza Arajo, R. de Oliveira, and V. E. Nascimento, “A dataset for evaluating intrusion detection systems in IEEE 802.11 wireless networks,” in Proceedings of the IEEE Colombian Conference on Communications and Computing, pp. 1-5, 2014. Google Scholar
- M. Ring, S. Wunderlich, D. Grdl, D. Landes, and A. Hotho, “Flow-based benchmark data sets for intrusion detection,” in Proceedings of the 16th European Conference on Cyber Warfare and Security, pp. 361-369, 2017. Google Scholar
- https://github.com/VishwaPrabhakar/MaliciousIPScanner/blob/master/goldeneye.pcap, Available: 2019/02/22, Available: 2019/02/22.
- https://github.com/somethingnew2-0/CS642-HW2/blob/master/traces/synflood.pcap, A vailable: 2019/02/22, Available: 2019/02/22.
- https://github.com/onty/trace-samples/blob/master/DIAMETER/ESy/EsyAndGy-Norma l.pcap, Available: 2019/02/22, Available: 2019/02/22.
- https://www.dropbox.com/sh/kk24ewnqi9qjdvt/AAAz0ySsffUi8B8yoPSE5kc3a/pcaps? dl=0, Available: 2019/02/22.
For more information about this article, please contact us here.