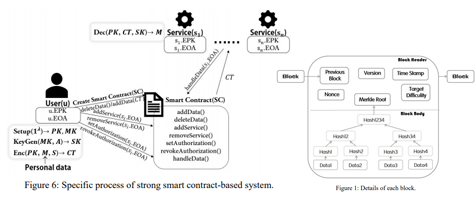
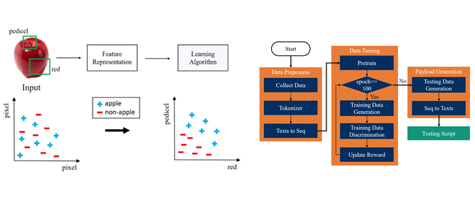
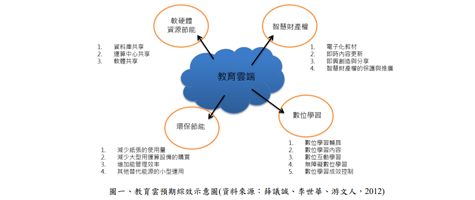
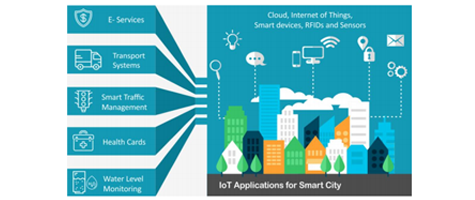
Smart Contract-based Decentralized Privacy System for Securing Data Ownership Management
Smart Contract-based Decentralized Privacy System for Securing Data Ownership Management*
Yunmin He1,2 , Yu-Chi Chen1* , Zhong-Yi Guo1 , Raylin Tso3 , and Shaozhen Ye2