Keywords: Automatic Web Security, Web Security Testing, Artificial Intelligence
Sheng-Xiang Lin1 , Hsin-Hung Cho2*
12Department of Computer Science and Information Engineering, National Ilan University
1 This email address is being protected from spambots. You need JavaScript enabled to view it., 2 This email address is being protected from spambots. You need JavaScript enabled to view it.
Abstract
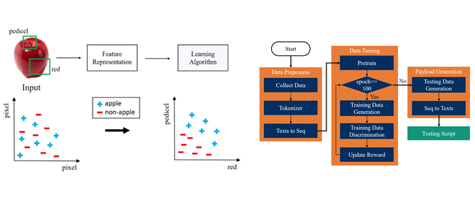
In the case of web security, the administrator usually prepares a large list of attack vectors when perform security testing. Some well-known free vulnerability scanning tools use a list of out-of-the-box attack vectors, while others generate attack vectors based on a known attack syntax format. Although this approach can save a lot of time and labor costs, it is able to only test problems which have been identified, and sometimes the success rate is not high. To increase the efficiency of security testing, we will try to increase the diversity of attack vectors to uncover more vulnerabilities. Therefore, we proposed an automatic security testing system by using artificial intelligence techniques. With the powerful search ability of artificial intelligence for unknown areas, it has the ability to generate pseudo-data features out of thin air so that the attack vectors can be learned and generated. We can take advantage of that to make a second choice to test the website for the administrator.
References
- S. Gorbunov and A. Rosenbloom, "AutoFuzz: Automated Network Protocol," International Journal of Computer Science and N etwork Security, pp. 239-245, August 2010. Google Scholar
- P. Godefroid, H. Peleg and R. Singh, "Fuzzing, Learn&Fuzz: Machine Learning for Input," in IEEE/ACM International Conference on Automated Software Engineering, UrbanaChampaign, Illinois, USA, 2017. Google Scholar
- B. P. Miller, L. Fredriksen and B. So, "An Empirical Study of the Reliability of UNIX Utilities," Communications of the ACM, vol. 33, no. 12, pp. 32-44, 1990.
- P. Hope and B. Walther, Web Security Testing Cookbook, O'Reilly Media, 2008. Google Scholar
- F. Yamaguchi, F. ’. Lindner and K. Rieck, "Vulnerability Extrapolation : Assisted Discovery of Vulnerabilities using Machine Learning," in WOOT'11 Proceedings of the 5th USENIX conference on Offensive technologies, San Francisco, CA, 2011. Google Scholar
- D. Wichers, "OWASP Top-10 2013," OWASP Foundation, 2013. Google Scholar
- D. Wichers, "Types of Cross-Site Scripting - OWASP," OWASP Foundation, [Online]. Available: https://www.owasp.org/index.php/Types_of_Cross-Site_Scripting.
- M. Meucci and A. Muller, "OWASP Testing Guide v4," OWASP Foundation, 2014.
- A. Radford, L. Metz and S. U. Chintala, "Unsupervised Representation Learning with Deep Convolutional Generative Adversarial Networks," in ICLR, 2016. Google Scholar
- L. Yu, W. Zhang, J. Wang and Y. Yu, "SeqGAN: Sequence Generative Adversarial Nets with Policy Gradient," in AAAI, 2017. Google Scholar
- O. E. David and N. S. Netanyahu, "DeepSign: Deep learning for automatic malware signature generation and classification," in International Joint Conference on Neural Networks, Killarney, Ireland, 2015. Google Scholar
- Y. Fang, Y. Li, L. Liu and C. Huang, "DeepXSS: Cross Site Scripting Detection Based on Deep Learning," in International Conference on Computing and Artificial Intelligence(ICCAI), 2018. Google Scholar
- A. C. Bahnsen, E. C. Bohorquez, S. Villegas, J. Vargas and F. A. González, "Classifying Phishing URLs Using Recurrent Neural Networks," in APWG Symposium on Electronic Crime Research, Scottsdale, AZ, USA, 2017. Google Scholar
- I. Takaesu, "Deep Exploit: Fully automatic penetration test tool using Machine Learning," in BlackHat, 2018.
- A. C. Bahnsen, I. Torroledo, L. D. Camacho and S. Villegas, "DeepPhish : Simulating Malicious AI," in APWG Symposium on Electronic Crime Research, 2018. Google Scholar
- F. Duchene, S. Rawat, J.-L. Richier and R. Groz, "KameleonFuzz: Evolutionary Fuzzing for Black-Box XSS Detection," in Proceedings of the 4th ACM Conference on Data and Application Security and Privacy, San Antonio, Texas, USA, 2014. Google Scholar
- D. Wichers, "XSS Filter Evasion Cheat Sheet - OWASP," OWASP Foundation, [Online]. Available: https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet.
- I. Tasdelen, "ismailtasdelen/xss-payload-list: Cross Site Scripting ( XSS ) Vulnerability Payload List," [Online]. Available: https://github.com/ismailtasdelen/xss-payload-list.
- A. Klein, "DOM Based Cross Site Scripting or XSS of the Third Kind," Web Application Security Consortium, 2005.
- I. Takaesu, "Method of detecting vulnerability in Web," in CODE BLUE, Tokyo, 2016.
For more information about this article, please contact us here