Keywords: Decentralized privacy system, Smart contracts, Encryption, Ownership, Access control.
Yunmin He1,2 , Yu-Chi Chen1* , Zhong-Yi Guo1 , Raylin Tso3 , and Shaozhen Ye2
1 Department of Computer Science and Engineering, Yuan Ze University, Taiwan
2 College of Mathematics and Computer Science, Fuzhou University, China
3 Department of Computer Science, National Chengchi University, Taiwan * This email address is being protected from spambots. You need JavaScript enabled to view it.
Abstract
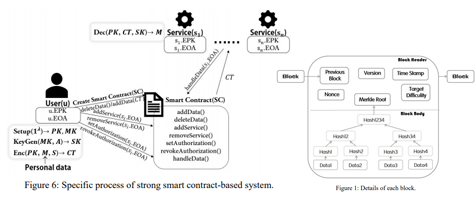
Recently, Zyskind et al. proposed a decentralized personal data management system which keeps privacy through blockchain and off-blockchain storage, so-called the decentralized privacy (DP) system. This system helps users ensure data ownership and fine-grained access control for third-party service providers. However, in this DP system, the permission power is delegated to blockchain and the users' data are stored in the off-blockchain distributed hashtable. Therefore, this induces extra communication overhead to connect these two distinct functionalities. In this paper, we present a conceptually simple solution directly from smart contracts with cryptographic primitives. This system is called the smart contract-based decentralized privacy (SCDP) system to overcome the above-mentioned efficiency issues. We propose the basic SCDP system as a warm-up to introduce the design principle based on symmetric encryption. Moreover, the strong SCDP system is provided by using ciphertextpolicy attribute-based encryption to support more flexible scenarios of access control and also eliminate some limitations of the basic system. Finally, we discuss some analyses in the aspects of security, access control, and data segmentation.
References
- A. Sahai and B. Waters, “Fuzzy identity-based encryption,” in Annual International Conference on the Theory and Applications of Cryptographic Technique. Springer, 2005, pp. 457–473. Google Scholar
- G. Wood, “Ethereum: A secure decentralised generalised transaction ledger,” Ethereum project yellow paper, vol. 151, pp. 1–32, 2014.
- G. Zyskind and O. Nathan, “Decentralizing privacy: Using blockchain to pro- tect personal data,” in Security and Privacy Workshops (SPW), 2015 IEEE. IEEE, 2015, pp. 180–184. Google Scholar
- J. Bethencourt, A. Sahai, and B. Waters, “Ciphertext-policy attribute-based encryption,” in Security and Privacy, 2007. SP’07. IEEE Symposium on. IEEE, 2007, pp. 321–334. Google Scholar
- J. Kehrli, “Blockchain 2.0-from bitcoin transactions to smart contract applications,” Niceideas, November. Available at:
https://www. niceideas.ch/roller2/badtrash/entry/blockchain-2-0-frombitcoin (Accessed:5 January 2018), 2016. - J. P. Cruz, Y. Kaji, and N. Yanai, “Rbac-sc: Role-based access control using smart contract,”IEEE Access, vol. 6, pp. 12 240–12 251, 2018. Google Scholar
- K. Christidis and M. Devetsikiotis, “Blockchains and smart contracts for the internet of things,” IEEE Access, vol. 4, pp. 2292–2303, 2016. Google Scholar
- K. Delmolino, M. Arnett, A. Kosba, A. Miller, and E. Shi, “Step by step towards creating a safe smart contract: Lessons and insights from a cryptocurrency lab,” in International Conference on Financial Cryptography and Data Security. Springer, 2016, pp. 79–94. Google Scholar
- K. Korpela, J. Hallikas, and T. Dahlberg, “Digital supply chain transformation toward blockchain integration,” in Proceedings of the 50th Hawaii international conference on system sciences, 2017. Google Scholar
- M. Haferkorn and J. M. Q. Diaz, “Seasonality and interconnectivity within cryptocurrencies-an analysis on the basis of bitcoin, litecoin and namecoin,” in International Workshop on Enterprise Applications and Services in the Finance Industry. Springer, 2014, pp. 106–120. Google Scholar
- N. Szabo, “Smart contracts,” Unpublished manuscript, 1994.
- P. McCorry, S. F. Shahandashti, and F. Hao, “A smart contract for boardroom voting with maximum voter privacy,” in International Conference on Financial Cryptography and Data Security. Springer, 2017, pp. 357–375. Google Scholar
- R. L. Rivest, A. Shamir, and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” Communications of the ACM, vol. 21, no. 2, pp. 120–126, 1978. Google Scholar
- S. King and S. Nadal, “Ppcoin: Peer-to-peer crypto-currency with proof-of-stake,” selfpublished paper, August, vol. 19, 2012. Google Scholar
- S. Nakamoto, “Bitcoin: A peer-to-peer electronic cash system,” 2008. Google Scholar
- V. Buterin, “A next-generation smart contract and decentralized application platform,” Google Scholar
- V. Goyal, O. Pandey, A. Sahai, and B. Waters, “Attribute-based encryption for finegrained access control of encrypted data,” in Proceedings of the 13th ACM conference on Computer and communications security. Acm, 2006, pp. 89–98. Google Scholar
- V. Jacynycz, A. Calvo, S. Hassan, and A. A. S ́anchez-Ruiz, “Betfunding: A distributed bounty-based crowdfunding platform over ethereum,” in Distributed Computing and Artificial Intelligence, 13th International Conference. Springer, 2016, pp. 403–411. Google Scholar
- V. Odelu, A. K. Das, M. K. Khan, K.-K. R. Choo, and M. Jo, “Expressive cp-abe scheme for mobile devices in iot satisfying constant-size keys and ciphertexts,” IEEE Access, vol. 5, pp. 3273–3283, 2017.Google Scholar
For more information about this article, please contact us here