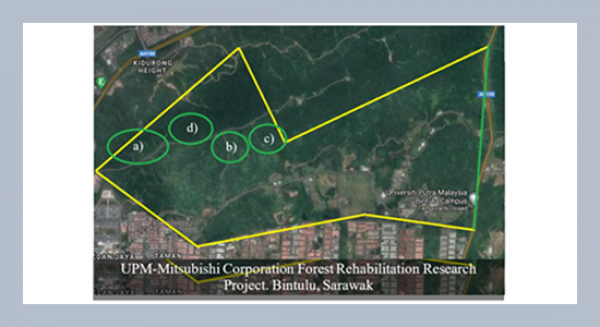
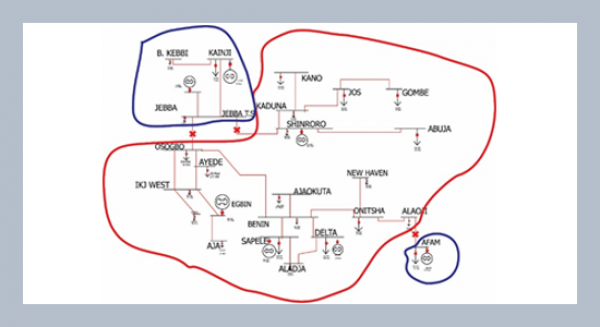
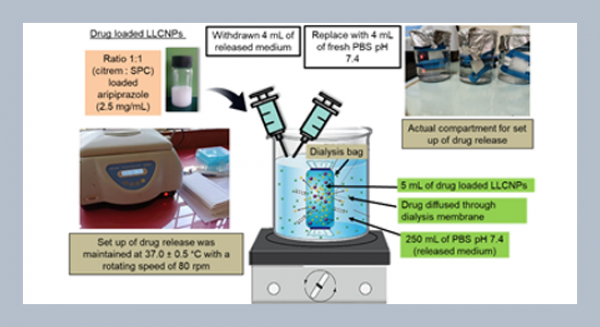
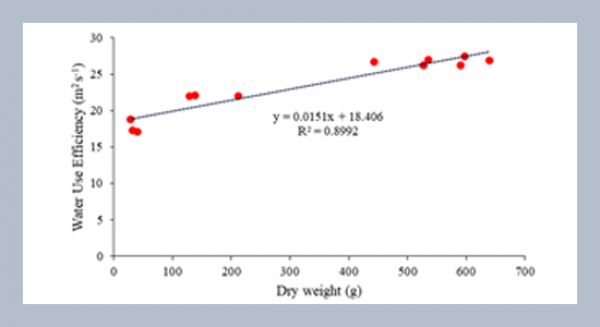
REFERENCES
- [1] Aho, A. V., Dahbura, A. T., Lee, D., and Uyar, M. U. 1991. An optimization technique for protocol conformance test generation based on UIO sequences and rural Chinese postman tours. IEEE Transactions on Communications, 39, 11: 1604-1615.
- [2] Ben-Ari, M. 1990. “Principles of Concurrent and Distributed Programming”. Prentice-Hall. Englewood Cliffs. New Jersey. U. S. A.
- [3] Chen, W. H. and Ural, H. 1995. Synchronizable test sequence based on multiple UIO sequences. IEEE/ACM Transactions on Networking, 3, 2: 152-157.
- [4] Chen, W. H., Tang, C. Y., and Vuong, S. T. 1995. Improving the UIOv- method for protocol conformance testing. Computer Communications, 18, 9: 609-612.
- [5] Chen, W. H. 1998. Test sequence generation from the protocol data portion based on the Selecting Chinese Postman Algorithm. Information Processing Letters, 65: 261-268.
- [6] Chen, W. H. 2001. Executable test sequence for the protocol data flow property. IFIP International Conference on Formal Techniques for Networked and Distributed Systems. Cheju Island. Korea.
- [7] Chow, T. S. 1989. Testing design modeled by finite state machines. IEEE Transactions on Software Enginering, 4: 178-186.
- [8] Dssouli, R., Saleh, K., Aboulhamid, E., En-Nouaary, A., and Bourhfir C. 1999. Test development for communication protocols: towards automation. Computer Networks, 31, 17: 1835-1872.
- [9] En-Nouaary, A., Dssouli, R., and Khendek, F. 2002. Timed Wp-method: testing real-time systems. IEEE Transactions on Software Engineering, 28, 11: 1130-1146.
- [10] Eswardan, K. E. and Tarjan, R. E. 1976. Augmentation Problems. SIAM Journal on Computing, 5, 4: 653-665.
- [11] Fujiwara, S., Bochmann, G. V., Khendek, F. Amalou, M., and Ghedamsi, A. 1991. Test selection based on finite state machine models. IEEE Transactions on Software Engineering, 17, 6: 591- 603.
- [12] Gill, A. 1962. “Introduction to the Theory of Finite State Machines”. McGraw Hill. New York.
- [13] Hsieh, E. P. 1971. Checking experiments for sequential machines. IEEE Transactions on Computing, 12, 10: 1024-1036.
- [14] International Standard Organization 1989. OSI Conformance Testing Methodology and Framework. ISO/IECJCT1/SC21 DIS 9646. Parts 4-5.
- [15] Kohavi, Z. 1978. “Switching and Finite Automata Theory”. MacGraw Hill. New York. U. S. A.
- [16] Lee, D. and Yannakakis, M. 1996. Principles and methods of testing finite state machines. Process of IEEE, 84, 8: 1090-1123.
- [17] Luo, G., Bochmann, G. V., and Petrenko,1994. Test selection based on communicating Nondeterministic Finite State Machines using a generalized Wp method. IEEE Transactions on Software Engineering, 12, 2: 120-132.
- [18] Miller, R. E. and Paul, S. 1993. On the generation of minimal-length conformance tests for communication protocols. IEEE/ACM Transactions on Networking, 1, 1: 116-129.
- [19] Naito, S. and Tsunoyama, M. 1981. Fault detection for sequential machines by transition tour. Process of IEEE Fault Tolerant Computing Sympsium.
- [20] Sabnani, K. K. and Dahbura, A. T. 1988. A protocol test generation procedure. Computer Networks and ISDN Systems, 15, 4: 285-297.
- [21] Sidhu, D. P. and Leung, T. K. 1988. Fault coverage of test methods. Process of IEEE INFOCOM.
- [22] Tanebaum, A. S. 1988. “Computer Network. Second Edition”. Prentice-Hall. Englewood Cliffs. New Jersey. U.S.A.
- [23] Vuong, S. T., Chan, W. Y. L., and Ito, M. T. 1989. The UIOv- method for protocol test sequence generation. Process of IFIP International Workshop on Protocol Test Systems. Berlin. Germany.