Keywords: International Forensic Standards, Construction Mobile forensics, Digital evidence, Digital (Cyber) forensics
I-Long Lin1,2†* Yingren Chen1
1Department of Information Management and Master’s Program in Digital Technology Innovation Management, Yuanpei University of Medical Technology
2Taiwan Association of Cyber Forensic Development (ACFD) 1 This email address is being protected from spambots. You need JavaScript enabled to view it.
Abstract
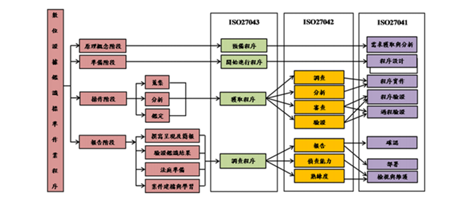
In view of our country's current legal system, the digital forensics (cyber) is not clear the special chapter legislation, the investigative agency are not in compliance with the norms, standards and procedures for the identification of digital (cyber), by collecting the literatures of the domestic and foreign digital (cyber) evidence, the digital (cyber) mechanism, the International standard operating procedure, and the ISO/IEC 27037:2012, ISO/IEC 27041:2015, ISO/IEC 27042:2015 and 27043:2015, the management of international standard procedures and guidelines, integrated digital forensics procedures to study the corresponding, based on the four stages (principle concept stage, preparation stage, operation stage, reporting stage) of the Digital Evidence Forensics Standard Operating Procedure (DEFSOP) presented by the domestic scholar Professor I-Long Lin, a complete set of Mobile Forensics standard operating procedures (DEFSOP for Mobile Forensics, DEFSOP- MF) is developed, Expect to the investigators and cyber personnel can understand the focus and direction of forensics (why to do) from the investigation process (what to do) and the investigation action (how to do) of the whole case, not only to strengthen the digital (cyber) evidence and proof, and to ensure the implementation of the security, enhance the digital (cyber) evidence in the court of evidence, proof and credibility of the target, but also in the future for the incidents to do an effective preventive mechanism and contingency disposal.
References
- ISO/IEC 27041:2015, “Information technology — Security techniques — Guidance on assuring suitability and adequacy of incident investigative method”, international standard, 2015. Google Scholar
- ISO/IEC 27042:2015,“Information technology — Security techniques — Guidelines for the analysis and interpretation of digital evidence”, international standard, 2015.
- ISO/IEC27043:2015, “Information Technology — Security Techniques —Investigation principles and processes”, international standard, 2015.
- Timothy Wright, The Field guide for investigation Computer Crime: search and seizure basic part three, security focus,2000.
- United States of Justice, Federal Guidelines for Searching and Seizing Computers, 1994.
- Warren G. Kruse II and Jay G. Heiser, Computer forensics-Incident Response Essentials, 2002, Addison-Wesley corporation. Google Scholar
- 方彥霏,2016,建構行動裝置數位證據鑑識標準作業程序之研究-從智慧型手機萃 取數位證據分析,國立宜蘭大學多媒體網路通訊數位學習碩士在職專班碩士論文。 Google Scholar
- 林宜隆、藍添興,2003,『數位證據蒐證程序之初探』,資訊管理學術暨警政資訊 實 務研討會, 中央警察大學主辦。
- 林宜隆,2006,建構網路犯罪行為模式之探討,檔案與微縮,第 82 期,頁 9-22。
- 林宜隆,2007,數位證據標準作業程序(DESOP)之建構,電腦稽核,第十六期。
- 林宜隆、歐啟銘,2008,手持式行動通訊裝置數位鑑識工具比之較與案例分析,第 十屆「網際空間:資安、犯罪與法律社會」學術研究暨實務研討會,輔仁大學主辦。
- 林宜隆,2009,網路犯罪理論與實務第三版,中央警察大學出版,桃園。
- 林宜隆、顏雲生、吳柏霖、蕭勝方,2010,「VoIP 攻擊分析與數位證據鑑識機制之 研究」,第二十一屆國際資訊管理學術研討會(ICIM 2010),台南市:成功大學。
- 林宜隆、李政謙、陳靜玉、張志汖,「數位證據鑑識標準作業程序與 ISO27037 數位 證據處理程序之比較分析」,2013 第十九屆資訊管理暨實務研討會。
- 林宜隆,「建構數位證據鑑識標準作業程序」,司法新聲101期_第 4 篇,2012,1 月。
- 林宜隆、張文耀、劉耿旭,「建構個人資料保護之數位證據鑑識標準作業程序」,電 腦稽核 27 期,2013 年 1 月。
- 陳詰昌,2016,數位鑑識「原件不可變動原則」之適用—由行動裝置鑑識與電腦鑑 識差異探討,第 119 期司法新聲季刊。
- 黃志龍,2006,建構數位證據鑑識標準作業程序規範之研究,中央警察大學碩士論 文。
- 黃敬博,2011,因應個資法之數位鑑識案例,第十屆台北國際資訊安全科技展暨亞 太資訊安全論壇。
- 楊鴻正,2003,我國資通安全鑑識科技能量規劃之研究,中央警察大學資訊管理所 論文。
- 劉秋伶,2010,數位證據之刑事證據調查程序,國立政治大學法律學研究所碩士論 文。
For more information about this article, please contact us here