Pinki Prakash Vishwakarma1*, Amiya Kumar Tripathy2, 3, Srikanth Vemuru1 1 Department of Computer Science and Engineering, Koneru Lakshmaiah Education Foundation, Andhra Pradesh, India
2 Department of Computer Engineering, Don Bosco Institute of Technology, Mumbai, India
3 School of Science, Edith Cowan University, Perth, Australia
Download Citation:
|
Download PDF
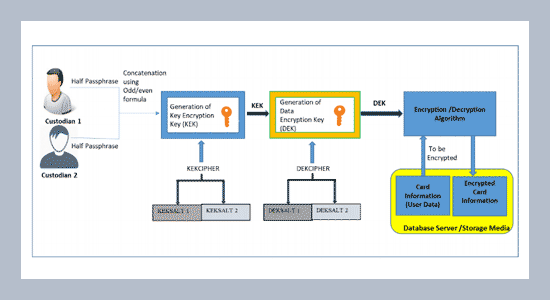
Since the evolution of m-commerce, security and entrustment of digitized transactions have become of captious concern to financial institutions. Card information hacking has caused money losses around the world, therefore it is imperative for financial institutions to get rid of such losses. Currently, the number of mobile payment schemes have been purposed but primarily the schemes aim attention at transaction security, fraud detection and prevention, not on data at rest encryption in mobile payments. Therefore, this work aims attention to encrypt sensitive static data residing at database server in mobile payments. Data at rest is the static data i.e., card details of the users which resides at the server. It is essential to ensure that the sensitive data of the payment users stay protected so as to prevent the adversaries looking for unauthorized access to the data. The encryption of data at rest is accomplished at the database level in this work. Cryptography is increasingly being used to combat against the security of sensitive data to guarantee data confidentiality and data integrity. In this work a cryptosystem is proposed which describes the management of cryptographic keys of the sensitive data at rest, in a mobile payment system with symmetric cryptographic implementation, the keys involved are identical for both encrypting and decrypting the sensitive data.ABSTRACT
Keywords:
Data confidentiality, Integrity, Encryption, Key management, Mobile payments.
Share this article with your colleagues
REFERENCES
ARTICLE INFORMATION
Received:
2020-03-31
Revised:
2020-08-21
Accepted:
2020-09-26
Available Online:
2020-12-01
Vishwakarma, P.P., Tripathy, A.K., Vemuru, S. 2020. Designing a cryptosystem for data at rest encryption in mobile payments. International Journal of Applied Science and Engineering, 17, 373–382. https://doi.org/10.6703/IJASE.202012_17(4).373
Cite this article:
Copyright The Author(s). This is an open access article distributed under the terms of the Creative Commons Attribution License (CC BY 4.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are cited.