Fawaz Alanazi 1, Ahmed Badi Alshammari 2, Chams Sallami 1, Asma A. Alhashmi 1, Rachid Effghi 3, Anil Kumar KM 4, Abdulbasit Darem 5 1 Department of Computer Science, College of Science, Northern Border University, Arar, Saudi Arabia 2 Department of Computer Science, College of Computing and Information Technology, Northern Border University, Saudi Arabia 3 Department of Big Data Analytics and Management, Bahcesehir University, Türkiye 4 JSS Science and Technology University, Department of Computer Science and Engineering, Mysuru, India 5 Center for Scientific Research and Entrepreneurship, Northern Border University, Arar, Saudi Arabia
Download Citation:
|
Download PDF
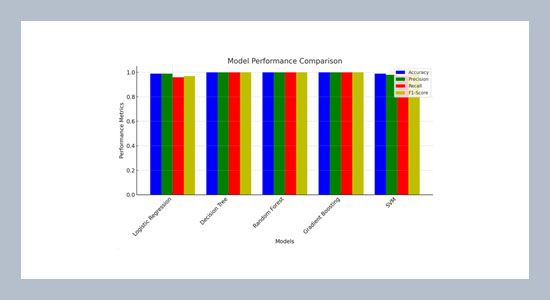
In today’s highly connected digital environment, effectively managing cybersecurity vulnerabilities is essential to protecting organizational systems. This research examines the use of machine learning models to predict the severity of vulnerabilities, utilizing data from the 2022, Cybersecurity and Infrastructure Security Agency (CISA) known exploited vulnerabilities catalogue. The study evaluates five machine learning models–Logistic Regression, Decision Tree, Random Forest, Gradient Boosting, and Support Vector Machine–based on their performance in terms of accuracy, precision, recall, and computational efficiency. The results show that tree-based models, especially Decision Tree, Random Forest, and Gradient Boosting, achieved perfect accuracy (100%) in categorizing vulnerabilities by severity, outperforming Logistic Regression and Support Vector Machine, which faced difficulties with critical vulnerabilities. Additionally, tree-based models demonstrated superior computational efficiency, with Decision Tree standing out in terms of both speed and accuracy, making it ideal for real-time use. The study emphasizes the potential of machine learning to automate and improve vulnerability management, allowing security teams to prioritize significant threats and better allocate resources. Future work should focus on incorporating real-time data and exploring deep learning methods to enhance model adaptability and performance. Overall, the research highlights the importance of machine learning in bolstering cybersecurity defenses.ABSTRACT
Keywords:
Cybersecurity, Machine learning models, Threat prioritization, Vulnerability management, Vulnerability severity prediction.
Share this article with your colleagues
REFERENCES
ARTICLE INFORMATION
Received:
2025-01-21
Revised:
2025-02-21
Accepted:
2025-03-09
Available Online:
2025-03-23
Alanazi, F., Alshammari, A.B., Sallami, C., Alhashmi, A.A., Effghi, R., Kumar, A., Darem, A. 2025. Enhancing cybersecurity vulnerability detection using different machine learning severity prediction models. International Journal of Applied Science and Engineering, 22, 2025013. https://doi.org/10.6703/IJASE.202503_22(1).003
Cite this article:
Copyright The Author(s). This is an open access article distributed under the terms of the Creative Commons Attribution License (CC BY 4.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are cited.