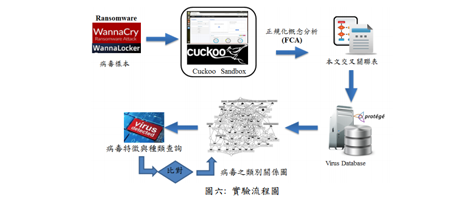
Keywords: Ontological Model Ransomware, Ontology, FCA, Cuckoo, Attack vector
Hsiao-Chung Lin1, Ping Wang2* , Wei-Qian, Hong3
1 ,2, 3Department of Information Management, Kun Shan University, Tainan, Taiwan
1This email address is being protected from spambots. You need JavaScript enabled to view it., 2This email address is being protected from spambots. You need JavaScript enabled to view it., 3This email address is being protected from spambots. You need JavaScript enabled to view it.
Abstract
The growing popularity of employing of the mobile device enables the development of the Internet of Thing (IoT). Generally, IoT devices use an embedded operating system, cannot completely install anti-virus engines, and uers have not continuously updated the operating system. Consequently, system vulnerabilities prone to attacks and may lead to the privacy of business or personal information leakage. Accordingly, the present study proposes an IoT-based security defence system with Raspberry Pi to analyse the attack vectors of Ransomware using Cuckoo malware dynamic analysis platform. Importantly, an ontology-based method for developing domain ontologies using Formal Concept Analysis (FCA) technique is proposed. Experimental data show that our model is capable of performing the missions including of i) explicitly identifying the relations between Ransomware and their malicious behavior , ii) categorizing the Ransomware and the variations, and (iii) assist manager analyse the security controls for virus protection from cyber threats.
References
- https://zh.wikipedia.org/wiki/WannaCry (2018/7/28)
- HoneyNet, “Cuckoo Sandbox”, https://github.com/ cuckoosandbox/cuckoo (2018/8/13)
- Y. Nativ, “GitHub- ytisf/theZoo: A repository of LIVE malwares for your own joy and pleasure” https://github.com/ytisf/theZoo (2018/8/01)
- Standard University, Protégé, https://protege.stanford.edu/(2018/7/11)
- C. Willems, T. Holz, and F. Freiling, “Toward automated dynamic malware analysis using CWSandbox, ” IEEE Security & Privacy, vol. 5, no. 2, pp. 32-39, 2007. Google Scholar
- Z. Tzermias, G. Sykiotakis, M. Polychronakis, and E. P. Markatos, “Combining static and dynamic analysis for the detection of malicious documents, in Proceedings of the Fourth European Workshop on System Security. 2011, ACM: Salzburg, Austria. pp. 1-6. Google Scholar
- N.F. Noy, D.L. McGuinness. “Ontology Development 101: a guide to creating your first ontology”, Stanford Knowledge Systems Laboratory Technical Report KSL-01-05, 2001. Google Scholar
- M. Uschold, M. Grueninger, “Ontologies: principles, methods and applications”, Knowledge Engineering Review, vol. 11, no.2, pp. 93-155, 1996. Google Scholar
- H. D. Huang, “Ontology-based intelligent system for malware behavioral analysis”, WCCI 2010 IEEE World Congress on Computational Intelligence, July, 18-23, Barcelona, Spain, 2010. Google Scholar
- http://en.wikipedia.org/wiki/ Formal_concept_ analysis. (2018/8/7)
- T. Priss, “Formal Concept Analysis in Information Science”. 2005, http://www.upriss. org.uk/fca/fca.html. (2018/8/7)
- S. Yevtushenko, “The Concept Explorer” , http://conexp.sourceforge.net/ (2018/8/13)
- TechNews,“史上第一勒索蠕蟲 WannaCry / Wcry 大舉入侵,趨勢科技教你週一拒 當資安人質”, 2017 年 05 月 15 日,http://technews.tw/2017/05/15/ wannacry-wcrykeep-watch/ (2018/7/28)
- 陳鷖人,“勒索病毒襲台 台電也中鏢”,中時電子報, 2017 年 05 月 15 日, https://www.chinatimes.com/realtimenews/20170515003208-260405?chdtv (2018/7/29)
- 林建宏、方國定,“正規化概念分析建構電腦病毒特徵之知識本體”,國立雲林科技 大學資訊管理系碩士論文,2009。
- Trend Labs 趨勢科技全球技術支援與研發中心, “勒索病毒 ransomware /勒索軟體”, 2015 年 02 月 01 日, https://blog. trendmicro.com.tw /?cat=2267 &paged=8 (2018/8/7)
- 戚玉樑,“以本體技術為基礎的知識庫建置程序及其應用”,資訊科技與社會,第五 卷第二期”. 2005,頁 1~18。 Google Scholar
- 王平、王宇治,“行動裝置病毒知識本體雛型之建構-以 Android 系統為例”,第 24 屆國際資訊管理學術研討會 (ICIM2013),真理大學, 2013。 Google Scholar
- 黃盈豪, 許通安,“以知識本體為基礎建構病毒分類知識庫系統”,中原大學資訊管 理研究所碩士論文, 2007。 Google Scholar
- 亞俊、孫宏民,“核心層即時 Android 惡意軟體偵測之研究”,國立清華大學資訊系 統與應用研究所碩士論文,2012。
- 謝維揚、曾文貴,“ MalCatcher:以存取以及網路洩漏隱私資料行為為基礎的 Android 惡意程式行為偵測”,國立交通大學網路工程研究所碩士論文,2013。 Google Scholar
- 鄧全良、徐雄健,“以虛擬程式載入器及病毒行為模式分析法的防毒系統”,銘傳大 學 資訊工程學系碩士論文, 2004。
- 張世杰、洪士灝,“Ape: Android 系統惡意程式之自動化測試環境”,國立臺灣大學 資訊工程學研究所碩士論文,2013。 Google Scholar
- 吳廸、林大為,“惡意程式碼的檢測研究”,健行科技大學資訊工程所碩士論文, 2013。 Google Scholar
- https://buzzorange.com/techorange/2017/05/15/trendmicro-wannacry/. (2019/3/9)
- https://applealmond.com/posts/5171
For more information about this article, please contact us here