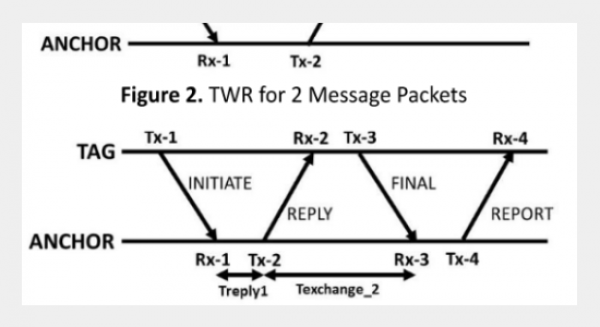
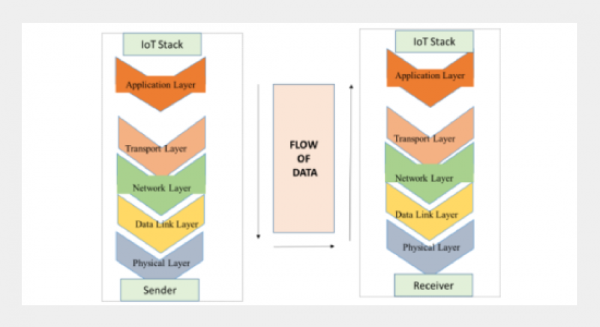
REFERENCES
- [1] Hezam Akram Abdul-Ghani and Dimitri Konstantas, A Comprehensive Study of Security and Privacy Guidelines, Threats, and Countermeasures: An IoT Perspective , Journal of sensor and actuator networks., April 2019,8(2):38. https://doi.org/10.3390/jsan8020022
- [2] Jithin R,Priya Chandran, Secure Dynamic Memory Management Architecture for Virtualization Technologies in IoT Devices, future internet, mdpi,Vol.10, Nov.2018, 119-225. https://doi.org/10.3390/fi10120119
- [3] Simone Cirani, Gianluigi, Enforcing Security Mechanisms in the IP-Based Internet of Things: An Algorithmic Overview, algorithms, mdpi, April 2013,197-226. https://doi.org/10.3390/a6020197
- [4] Dzevdan Kapetanovic, Gan Zheng, Fredrik Rusek, Physical layer security for massive MIMO: An overview on passive eavesdropping and active attacks, IEEE Communications Magazine, Volume: 53 Issue: 6, June 2015, 21- 27. https://doi.org/10.1109/MCOM.2015.7120012
- [5] M. Daniel, "Hidden Dangers of Internet of Things", Women in Security, pp. 69-75, 2017. https://doi.org/10.1007/978-3-319-57795-1_7
- [6] A. Al-Gburi, A. Al-Hasnawi and L. Lilien, "Differentiating Security from Privacy in Internet of Things: A Survey of Selected Threats and Controls", Computer and Network Security Essentials, pp. 153-172, 2017. https://doi.org/10.1007/978-3-319-58424-9_9
- [7] B. Payne and T. Abegaz, "Securing the Internet of Things: Best Practices for Deploying IoT Devices", Computer and Network Security Essentials, pp.493-506, 2017. https://doi.org/10.1007/978-3-319-58424-9_28
- [8] Shruti Jaiswal and D. Gupta, "Security Requirements for Internet of Things (IoT)", Advances in Intelligent Systems and Computing, pp. 419-427, 2017. https://doi.org/10.1007/978-981-10-2750-5_44
- [9] M.Shainika, Mrs.C.Hema "Cluster Based Mobile Key Management Scheme to Improve Scalability and Mobility in Wireless Sensor Networks", National Conference on Research Advance in communication, computation, electrical science and structure, ISSN- 2348-8387, Nov 2015
- [10] Maryam Sabet, Hamid RezaNaj "A decentralized energy efficient hierarchical cluster-based routing algorithm for wireless sensor networks", Volume 69, Issue 5, May 2015, pp. 790-799. https://doi.org/10.1016/j.aeue.2015.01.002
- [11] Pavithra G.S., Babu N.V, "Energy Efficient Hierarchical Clustering using HACOPSO in Wireless Sensor Networks", International Journal of Innovative Technology and Exploring Engineering, Vol-8 Issue-12, October, 2019. https://doi.org/10.35940/ijitee.L2789.1081219
- [12] Rafael F. Schaefer, Gayan Amarasuriya, H. Vincent Poor , Physical layer security in massive MIMO systems, Asilomar Conference on Signals, Systems, and Computers, April 2018. https://doi.org/10.1109/ACSSC.2017.8335124
- [13] Dimitriya, Ziatka, Georgi, Vladimir ,Shifted 2-N-PSK Method for the Detection of Pilot Contamination Attacks, wireless personal communications, April 2019,1-26.
- [14] Muhammad Asim Khan, Mansoor Khan, A Review on Security attacks and solutionin Wireless Sensor Networks, American Journal of Computer Science and Information Technology, Vol.7 Feb 2019, 1-31.
- [15] Mac, F.; St, F.; Quisquater, J. ASIC Implementations of the Block Cipher SEA for Constrained Applications. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.88.926
- [16] Pecorella, T., Brilli, L., & Mucchi, L. . The role of physical layer security in IoT: A novel perspective. Information,January 2016 7(49), 1-17. https://doi.org/10.3390/info7030049
- [17] Feroz Khan, A.B. & Anandharaj, G. "A cognitive key management technique for energy efficiency and scalability in securing the sensor nodes in the IoT environment: CKMT", SN Appl. Sci. (2019) 1(12):1575. https://doi.org/10.1007/s42452-019-1628-4
- [18] Tariq Aziz Rao, Ehsan-ul-Haq, Security Challenges Facing IoT Layers and its Protective Measures, International Journal of Computer Applications (0975 - 8887) Volume 179 - No.27, March 2018. https://doi.org/10.5120/ijca2018916607
- [19] T. Heer, O. Garcia-Morchon, R. Hummen, S. L. Keoh, S. S. Kumar, K. Wehrle, "Security challenges in the ip- based internet of things", Wireless Personal Communications, vol. 61, no. 3, pp. 527-542, 2011. https://doi.org/10.1007/s11277-011-0385-5
- [20] Mohsen Nia, A.; Jha, N.K. A Comprehensive Study of Security of Internet-of-Things. IEEE Trans. Emerg.Top. Comput. 2017, 5, 586-602. https://doi.org/10.1109/TETC.2016.2606384
- [21] Guzman, A. IoT Penetration Testing Cookbook; Packt Publishing: Birmingham, UK, 2017.
- [22] UL LLC. List of IOT Security Top 20 Design Principles; White Paper; UL LLC: Northbrook, IL, USA, 2017.
- [23] Emil Bjohnson, PILOT CONTAMINATION IN A NUTSHELL, www.ma-mimo.ellintech.se/, January 2017.
- [24] Eastlake, D.E.; Jones, P.E. US Secure Hash Algorithm 1 (SHA1). Available online: http://www.ietf.org/rfc/rfc3174.txt
- [25] Shital Patil, Sangita Chaudhari, DoS Attack Prevention Technique in Wireless Sensor Networks, ScienceDirect, 7th International Conference on Communication, Computing and Virtualization 2016. https://doi.org/10.1016/j.procs.2016.03.094
- [26] Q. Zhou, J. Zhang, "Research prospect of Internet of Things geography", Proceedings of the 19th International Conference on Geoinformatics, pp. 1-5, 2011. https://doi.org/10.1109/GeoInformatics.2011.5981045
- [27] M. Panda, "Security threats at each layer of wireless sensor networks", International Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, pp. 50-56, 2013.
- [28] Puthal D., Ranjan R., Nepal S., Chen J. (2018) IoT and Big Data: An Architecture with Data Flow and Security Issues. In: Longo A. et al. (eds) Cloud Infrastructures, Services, and IoT Systems for Smart Cities. IISSC 2017, CN4IoT 2017. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 189. https://doi.org/10.1007/978-3-319-67636-4_25
- [29] Tommaso Pecorella, Luca Brilli , Lorenzo Mucchi, The Role of Physical Layer Security in IoT: A Novel Perspective, Information No.3, Vol.7, August2016, 7(3). https://doi.org/10.3390/info7030049
- [30] Nick Ismail, The future of the 'Internet of Things' security issues, www.information-age.com, December 2017.