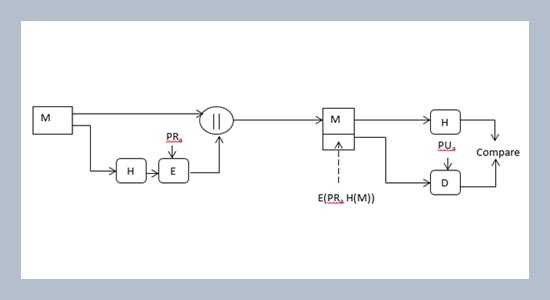
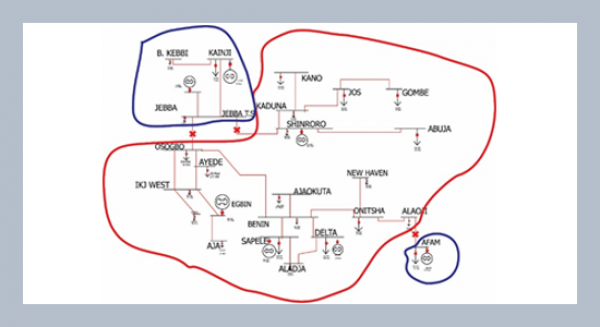
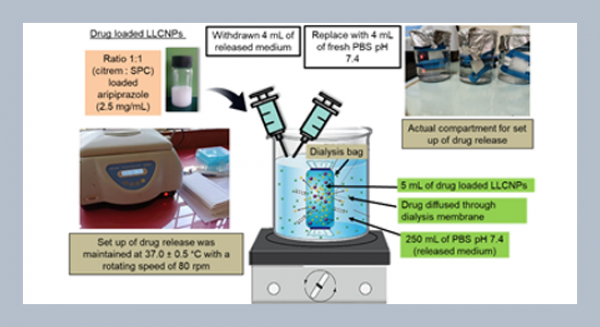
REFERENCES
- Badotra, S., Panda, S.N. 2019. Evaluation and comparison of OpenDayLight and open networking operating system in software-defined networking. Cluster Computing, 1–11.
- Badotra, S., Panda, S.N. 2020. A survey on software defined wide area network. International Journal of Applied Science and Engineering, 17, 59–73.
- Badotra, S., Panda, S.N. 2020. Experimental comparison and evaluation of various OpenFlow software defined networking controllers. International Journal of Applied Science and Engineering, 17, 317–324.
- Badotra, S., Singh, J. 2017. A review paper on software defined networking. International Journal of Advanced Research in Computer Science, 8.
- Badotra, S., Singh, J. 2017. Open daylight as a controller for software defined networking. International Journal of Advanced Research in Computer Science, 8.
- Badotra, S., Singh, J. 2019. Creating firewall in transport layer and application layer using software defined networking. In Innovations in Computer Science and Engineering, 95–103. Springer, Singapore.
- Badotra, S., Nagpal, D., Panda, S.N., Tanwar, S., Bajaj, S. 2020. IoT-enabled healthcare network with SDN. In 2020 8th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), 38–42. IEEE.
- Bi, W., Jia, X., Zheng, M. 2018. A secure multiple elliptic curves digital signature algorithm for blockchain. arXiv preprint arXiv:1808.02988.
- Buenasmañanas Domínguez, F.J., Encinas, A.H., Queiruga Dios, A., Hernández Encinas, L. 2011. Digital identity-based multisignature scheme implementation. The First International Conference on Advanced Communications and Computation (INFOCOMP 2011), 42–45.
- Chen, T.S., Huang, K.H., Chung, Y.F. 2004. Digital multi-signature scheme based on the elliptic curve cryptosystem. Journal of Computer Science and Technology, 19, 570–573.
- Devi, D.S., Thilagavathy, K., Krishnan, P.S. 2015. An efficient and secure digital multi-signature protocol based on ECC. International Journal on Cryptography and Information Security (IJCIS), 5.
- Devi, D.S., Sudendar, S. 2015. Privacy preserving analytics in outsourced healthcare system. International Journal of Innovative Technology and Exploring Engineering (IJITEE), 9.
- Gangishetti, R., Gorantla, M.C., Das, M.L., Saxena, A. 2006. Identity based multisignatures. Informatica, 17, 177–186.
- Harn, L., Ren, J. 2008. Efficient identity-based RSA multisignatures. computers & security, 27, 12–15.
- ISO/IEC 14888-3, 1998. Information technology – securitytechniques – digital signatures with appendix. Part 3: Certificatebased-mechanisms, International Organization for Standardization, Geneva.
- Koblitz, N. 1987. Elliptic curve cryptosystems. Mathematics of computation, 48, 203–209.
- Mehibel, N., Hamadouche, M.H. 2021. Authenticated secret session key using elliptic curve digital signature algorithm. Security and Privacy, 4, p.e148.
- Miller, V.S. 1985. Use of elliptic curves in cryptography. In Conference on the theory and application of cryptographic techniques, 417–426. Springer, Berlin, Heidelberg.
- Negi, A., Sharma, P., Chaudhary, P., Gupta, H. 2015. New method for obtaining digital signature certificate using proposed RSA algorithm. International Journal of Computer Applications, 121, 24–29.
- Nia, M.A., Sajedi, A., Jamshidpey, A. 2014. An introduction to digital signature schemes. arXiv preprint arXiv:1404.2820.
- Saritha, K. 2020. Block chain authentication using elliptic curve digital signature algorithm.
- Shamir, A. 1984. Identity-based cryptosystems and signature schemes. In Workshop on the theory and application of cryptographic techniques, 47–53. Springer, Berlin, Heidelberg.
- Shobha, G., Rana, A., Kansal, V., Tanwar, S. 2021. Code clone detection—A systematic review. Emerging Technologies in Data Mining and Information Security, 645–655.
- Sharma, R., Mogha, M., Tanwar, S., Rana, A. 2020. Emerging part of industry 4.0: The digital and physical technology. In 2020 9th International Conference System Modeling and Advancement in Research Trends (SMART) (149–154). IEEE.
- Singh, A.K., Solanki, A., Nayyar, A., Qureshi, B. 2020. Elliptic curve signcryption-based mutual authentication protocol for smart cards. Applied Sciences, 10, 8291.
- Tanwar, S. 2017. A new pairing free ID based certificate less digital signature (CL-DS) scheme using elliptic curve cryptography. International Journal of Computer Science and Information Security (IJCSIS), 15.
- Tanwar, S., Kumar, A. 2019. An efficient and secure identity based multiple signatures scheme based on RSA. Journal of Discrete Mathematical Sciences and Cryptography, 22, 953-971.
- Thu, A.A., Mya, K.T. 2014. Implementation of an efficient blind signature scheme. International Journal of Innovation, Management and Technology, 5, 443.
- Tianhuang, C., Xiaoguang, X. 2010. Digital signature in the application of e-commerce security. In 2010 International Conference on E-Health Networking Digital Ecosystems and Technologies (EDT), 1, 366–369. IEEE.
- Tsai, C.H., Su, P.C. 2017. An ECC-based blind signcryption scheme for multiple digital documents. Security and Communication Networks.
- Wang, X., Bai, Y., Hu, L. 2015. Domain based certification and revocation. In Proceedings of the International Conference on Security and Management (SAM), 272–278. The Steering Committee of the World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
- Yadav, N., Tanwar, S. 2013. Implementation of white-box cryptography in credit card processing combined with code obfuscation. International Journal of Computer Applications, 70.
- Yang, F.Y., Lo, J.H., Liao, C.M. 2013. Improving an efficient ID-based RSA multisignature. Journal of Ambient Intelligence and Humanized Computing, 4, 249–254.