Guttikonda Prashanti 1*, P Ashok Kumar 2, Popuri Keerthika 3 1 Department of Advanced Computer Science and Engineering, Vignan’s Foundation for Science, Technology and Research, Vadlamudi, Guntur, AP, India 2 Department of Chemical Engineering, Vignan’s Foundation for Science, Technology and Research, Vadlamudi, Guntur, AP, India 3 Department of CSE, R.V.R. and J.C., College of Engineering, Chowdavaram, Guntur, AP, India
Download Citation:
|
Download PDF
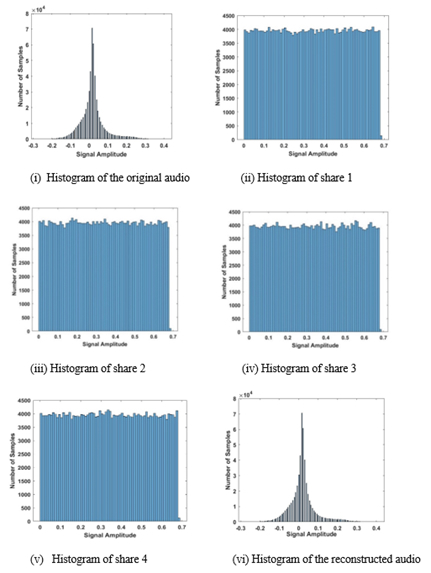
Polynomial-based secret sharing is a tool used to secure a secret that is being shared by a group of users. Dealer, through a private channel, distributes shadows of the secret to users in the group, and only the threshold number of users with their shadows can retrieve the secret. However, some users provide fake shadows so that the original secret cannot be retrieved. Identifying such cheating behavior is important while reconstructing the secret. This article introduces a novel method for audio-based secret sharing using polynomials. The proposed technique not only enables the creation of smaller-dimensional audio shares but also incorporates a mechanism to identify untrustworthy participants within the group. Our proposed method employs dual security measures to ensure the integrity and authenticity of the audio-sharing process. Firstly, our method includes a verification process to authenticate whether the dealer has indeed derived the audio share using the participant's true secret value. Through this approach, participants can ensure the integrity and authenticity of the audio shares published by the dealer. Secondly, another set of verification codes is generated to enable participants to validate each other's submitted secret values, preventing fraudulent submissions during the reconstruction process. By employing this dual approach, security is enhanced through the implementation of multiple layers of verification and authentication across the entire process.ABSTRACT
Keywords:
Checksum, Confidentiality, Discrete logarithms, Generator, Lagrange interpolation, Untrustworthy participants.
Share this article with your colleagues
REFERENCES
ARTICLE INFORMATION
Received:
2024-07-12
Revised:
2024-12-23
Accepted:
2025-02-16
Available Online:
2025-03-17
Prashanti, G., P, A.K., Keerthika, P. 2025. Ensuring dealer and participant truthfulness in the audio share generation and reconstruction processes for an audio secret sharing scheme. International Journal of Applied Science and Engineering, 22, 2024232.https://doi.org/10.6703/IJASE.202503_22(1).002
Cite this article:
Copyright The Author(s). This is an open access article distributed under the terms of the Creative Commons Attribution License (CC BY 4.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are cited.