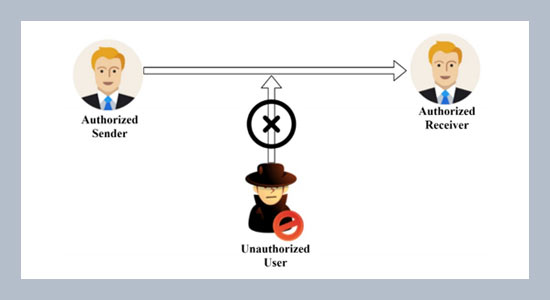
REFERENCES
- Aïmeur, E., Schőnfeld, D. 2011. The ultimate invasion of privacy: Identity theft. Ninth Annual International Conference on Privacy, Security, and Trust, 24–31. IEEE.
- Al-Slamy, N.M. 2008. E-commerce security. International Journal of Computer Science and Network Security, 8, 340.
- Amarasekara, B.R., Mathrani, A. 2016. Controlling risks and fraud in affiliate marketing: A simulation and testing environment. 14th Annual Conference on Privacy, Security and Trust (PST) 353–360. IEEE.
- Archana, T.S. 2020. E-cash payments and security threats. Studies in Indian Place Names, 40, 386–392.
- Atlantic BT, 1999-2020. https://www.atlanticbt.com/insights/how-much-does-ecommerce-website-cost/ Accessed on 12th March 2020
- Azmi, I.M.A.G., Phuoc, J.C. 2020. International norms in regulating ecommerce: The electronic commerce chapter of the comprehensive Trans-Pacific partnership agreement. International Journal of Business & Society, 21, 66–80.
- Banday, M.T., Qadri, J.A. 2011. Phishing-A growing threat to E-comemrce. The Business Review, 12, 76–83.
- Basul, A. 2018. 5 types of fraud that is used to target E-commerce retailers. https://www.ravelin.com/blog/5-types-of-fraud-that-is-used-to-target-E-comemrce-retailers, Access on 9th March 2020.
- Big Commerce Pty. Ltd., 2020. https://www.bigcommerce.com/blog/ecommerce-website-security/ Accessed on 12th March 2020.
- Blakley, B., Blakley, G.R. 2000. All sail, no anchor, I: Cryptography, Risk, and E-comemrce. In Australasian Conference on Information Security and Privacy, 471–476. Springer, Berlin, Heidelberg.
- Cai, S., Xu, Y. 2008. Designing product lists for E-comemrce: The effects of sorting on consumer decision making. International Journal of Human–Computer Interaction, 24, 700–721.
- Cater-Steel, A., Grist, S. 2006. e-Commerce definition dilemma. In: Encyclopedia of developing regional communities with information and communication technology. Information Science Reference (IGI Global), Hershey, PA, United States, 152–158. ISBN 1-59140-575-0.
- Chen, J.C., Chiniwar, S., Lin, B., Chen, P. 2006. Security in e-business and beyond: a case study reflecting current situations and future trends. International Journal of Mobile Communications, 4, 17–33.
- Chomsiri, T. 2007, May. HTTPS hacking protection. 21st International Conference on Advanced Information Networking and Applications Workshops (AINAW'07) 1, 590–594. IEEE.
- Cimpanu, C. for Zero Day, 2019. https://www.zdnet.com/article/wordpress-accounted-for-90-percent-of-all-hacked-cms-sites-in-2018/Accessed on 13th March 2020.
- Cobweb Security, 2020. 5 Main reasons why your website is sending spam, https://cobweb-security.com/security_lessons/5-main-reasons-why-your-website-is-sending-spam/, Accessed on 10th March 2020.
- Dahiya, A., Gupta, B.B. 2020. DDoS attacks detection and mitigation using economic Incentive-Based solution. In First International Conference on Sustainable Technologies for Computational Intelligence, 729–738. Springer, Singapore.
- DataDome, 2020. https://datadome.co/bot-management-protection/brute-force-bot-attacks-how-to-protect-websites-and-apps/, accessed on 10th March 2020.
- Dhobe, S.D., Tighare, K.K., Dake, S.S. 2020. A review on prevention of fraud in electronic payment gateway using secret code, International Journal of Research in Engineering, Science and Management, 3, 602–606.
- Dimension, 2020, Source: https://www.dimensions.ai/access on: 7th March 2020
- Duh, R.R., Sunder, S., Jamal, K. 2002. Control and assurance in E-comemrce: Privacy, integrity, and security at eBay. Taiwan Accounting Review, 3, 1–27.
- Egger, F.N. 2000. "Trust me, I'm an online vendor" towards a model of trust for E-commerce system design, available at: www.zurich.ibm.com/~mrs/chi2000/contributions/ egger.html (accessed January 20, 2021).
- Erbschloe, M. 2004. Trojans, worms, and spyware: a computer security professional's guide to malicious code. Elsevier.
- Ettredge, M., Richardson, V.J. 2002. Assessing the risk in E-comemrce. 35th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 11 pp.-, doi: 10.1109/HICSS.2002.994192
- Fletcher, N. 2007. Challenges for regulating financial fraud in cyberspace. Journal of Financial Crime, 14, 190–207. https://doi.org/10.1108/13590790710742672.
- Fraser, J., Fraser, N., McDonald, F. 2000. The strategic challenge of electronic commerce. Supply Chain Management: An International Journal, 5, 7–14.
- Free lock computing, 1995-2019. https://www.freelock.com/blog/john-locke/2011-09/hidden-costs-E-comemrce-sites Accessed on 12th March 2020.
- Fuller, M.A., Serva, M.A., Baroudi, J. 2009. Clarifying the integration of trust and TAM in E-commerce environments: implications for systems design and management. IEEE Transactions on Engineering Management, 57, 380–393.
- Furhad, M.H., Sadik, S., Ahmed, M. 2020. Exploring E-commerce In cyber security context through blockchain technology. Blockchain in Data Analytics, 216–233.
- Gehling, B., Stankard, D. 2005. eCommerce security. 2nd annual conference on Information security curriculum development, 32–37.
- Goel, R. 2007. E-Commerce. New Age International Ltd Publishers, 204.
- Gordon, J.R., Gordon, S.R. 1999. Information systems. A Management Approach, The Dryden Press, Hinsdale, IL.
- Guo, Y., Le-Nguyen, K., Jia, Q., Li, G. 2015. Seller-buyer trust in cross-border E-comemrce: Emergent Research Forum papers. Twenty‐first Americas Conference on Information Systems.
- Gupta, A., Tung, Y.A., Marsden, J.R. 2004. Digital signature: use and modification to achieve success in next generational e-business processes. Information & Management, 41, 561–575.
- Halaweh, M., Fidler, C. 2008. Security perception in E-comemrce: Conflict between customer and organizational perspectives. International Multiconference on Computer Science and Information Technology, 443–449. IEEE.
- Hamirani, E. 2020. The challenges for cyber security in E-comemrce. International Journal of Advance and Innovative Research, 7, ISSN 2394 - 7780.
- Hunt, R. 2001. Technological infrastructure for PKI and digital certification. Computer communications, 24, 1460–1471.
- Hutter, B., Power, M. 2000. Risk management and business regulation, London: Centre for analysis of risk and regulation, London school of economics and political acience, accessed 9th May 2020. ICAEW (1999a) Implementing Turnbull, London, UK: ICAEW.
- Immordino, G., Russo, F.F. 2018. Cashless payments and tax evasion. European Journal of Political Economy, 55, 36–43.
- Imperva, 2020, Cross site scripting (XSS) attacks Imperva, https://www.imperva.com/learn/application-security/cross-site-scripting-xss-attacks/, Access on 11th March 2020.
- Infisecure, https://www.infisecure.com/blogs/impact-bad-bots-ecommerce-industry, Accessed on 10th March 2020.
- Informa PLC Informa UK Limited, 2020, https://www.informationweek.com/mobile/mobile-devices/gartner-21-billion-iot-devices-to-invade-by-2020/d/d-id/1323081 Accessed on 10th March 2020.
- Jayanthi, R. 2020. E-commerce security based on cryptography and Encryption-A study, Journal of Information and Computational Science, ISSN: 1548-7741, 10, 453–463.
- Jing, Y. 2009. On-line payment and security of E-comemrce. The 2009 International Symposium on Web Information Systems and Applications (WISA 2009), 46.
- Jordan, T., Taylor, P.A. 2004. Hacktivism and cyberwars: Rebels with a cause?. Psychology Press.
- Kaspersky Lab, AO 2020, Black friday alert. https://securelist.com/black-friday-alert/88856/, Access on 11th March 2020.
- Kaspersky Lab, AO 2020, DDoS attacks in Q1 2019, Oleg Kupreev, Ekaterina Badovskaya, AlexanderGutnikov on May 21, 2019. https://securelist.com/ddos-report-q1-2019/90792/, Accessed on 12th March 2020.
- Kim, B.H., Kim, K.C., Hong, S.E., Oh, S.Y. 2017. Development of cyber information security education and training system. Multimedia Tools and Applications, 76, 6051–6064.
- Kim, H., Han, Y., Kim, S., Choi, M. 2005. A curriculum design for E-commerce security. Journal of Information Systems Education, 16, 55–64. Retrieved from https://search.proquest.com/scholarlyjournals/curriculum-design-e-commercesecurity/docview/200135706/se-2?accountid=147490.
- Kingpin, K., Mudge, M. 2001. Security analysis of the palm operating system and its weaknesses against malicious code threats. 10th conference on USENIX Security Symposium-10, 11–11.
- Kumar, S. 2020. Advantages and challenges of E-commerce in the Indian Banking System. Studies in Indian Place Names, 40, 4064–4071.
- Laitala, N. 2012. Hacktivism and cyberterrorism: human rights issues in state responses (Doctoral dissertation), https://doi.org/20.500.11825/740, Global Campus Open Knowledge Repository, Accessed on 11th January 2021.
- Lakhani, A.R. 2019. Top ecommerce security threats to online shopping sites, Magenticians, https://magenticians.com/ecommerce-security-threats/, Accessed on 11th March 2020.
- Li, H., Xue, W. 2020. Application of E-commerce network security technology. In Data Processing Techniques and Applications for Cyber-Physical Systems (DPTA 2019) 633–639. Springer, Singapore.
- Liu, T., Wang, Z. 2020. Practical problems in the customs supervision on Cross-Border E-commerce goods and its solutions. 5th International Conference on Economics, Management, Law and Education (EMLE 2019) 1013–1020.
- Loop54.com, 2020. https://www.loop54.com/blog/top-5-security-threats-facing-E-comemrce-today Accessed on 13th March 2020.
- Magneto IT Solutions, 2020. https://magnetoitsolutions.com/infographic/ecommerce-security Accessed on 11th March 2020.
- Malik, S.R., Rafiq, M., Kahloon, M.A. 2020. Cloud security in E-commerce applications. In Cloud Computing Applications and Techniques for E-commerce, 50–67.
- Murphy, J. 2000. Assuring performance in E-commerce systems. IEE 16th UK Teletraffic Symposium, 29.
- Nabi, F. 2005. Secure business application logic for E-commerce systems. Computers & Security, 24, 208–217.
- Nadeem, A., Javed, M.Y. 2005. A performance comparison of data encryption algorithms. International Conference on Information and Communication Technologies, 84–89. IEEE.
- Nanduri, J., Jia, Y., Oka, A., Beaver, J., Liu, Y.W. 2020. Microsoft uses machine learning and optimization to reduce E-commerce fraud. Interfaces, 50, 64–79.
- Nanduri, J., Liu, Y.W., Yang, K., Jia, Y. 2020. Ecommerce fraud detection through fraud islands and Multi-layer machine learning model. In Future of Information and Communication Conference, 556–570. Springer, Cham.
- O'Leary, D.E. 2000. Enterprise resource planning systems: systems, life cycle, electronic commerce, and risk. Cambridge university press.
- Oppliger, R., Hauser, R., Basin, D. 2008. SSL/TLS session-aware user authentication. Computer, 41, 59–65.
- Othman, A.K., Hassan, L.F.A., Ibrahim, M.A.M., Saripin, M.S., Sapuan, N.S.A., Roslan, Z.N. 2020. Factors that influence customer loyalty in using E-comemrce. Journal of Islamic Management Studies, 2, 43–58.
- Padmavathy, K., Kalyani, M.B. 2020. E-Cash payments and security. Studies in Indian Place Names, 40, 649–654.
- Park, J., Lee, D., Ahn, J. 2004. Risk-focused E-commerce adoption model: A cross-country study. Journal of Global Information Technology Management, 7, 6–30.
- Perlmutter, D. 2019. https://blog.cyberint.com/the-top-5-ecommerce-security-trends-of-2019 Accessed on 11th March 2020.
- Prasad, R., Rohokale, V. 2020. Cyber security: The Lifeline of Information and Communication Technology. Springer.
- Prasad, R., Rohokale, V. 2020. E-comemrce. In cyber security: The Lifeline of Information and Communication Technology, 175–185. Springer.
- Ramasubramanian, S., Prakash, P. 2013. Spam and internet abuse in India: A brief history. World Cyberspace Cooperation Summit IV (WCC4) 1–7. IEEE.
- Razvan, R., Edvard, O. 1790. On security of E-comemrce. Recent advance in mathematics and computer in business, Economics, Biology and Chemistry, ISSN, 2769.
- Retruster Ltd, 2019, 2019 Phishing statistics and email fraud statistics, retruster, https://retruster.com/blog/2019-phishing-and-email-fraud-statistics.html, Accessed on 12th March 2020.
- Rodríguez, G.E., Torres, J.G., Flores, P., Benavides, D.E. 2020. Cross-site scripting (XSS) attacks and mitigation: A survey. Computer Networks, 166, 106960.
- Sabatino, M. 2020. Crime treasure islands: Tax havens, Tax evasion and money laundering. Journal of Economics and Business, 3, Available at SSRN: https://ssrn.com/abstract=3530218.
- Saeed, S., Naqvi, M., Memon, M. 2020. E-commerce web crawling to facilitate consumers for economical choices. International Journal of Advanced Computer Systems and Software Engineering, 1, 1–13.
- Sai, Y., Income, A.C.O. Taxation International Taxation E-commerce Issues in Cyber Space, URL: http://nalsarpro.softpal.in/Portals/23/Courses/CL/Presentations/CL441.pdf, Accessed on 10th March 2020
- Salomon, D. 2010. Trojan horses. In Elements of Computer Security, 123–135. Springer.
- Samanta, B. 2020. Epidemic modelling for the spread of bots through DDoS attack in E-commerce network. In Handbook of Computer Networks and Cyber Security, 445–459. Springer.
- Schick, S. 2018, Security intelligence, Shane Schick on 7th May 2018, https://securityintelligence.com/news/new-cybercrime-statistics-1-billion-bots-involved-in-210-million-fraud-attempts-in-q1/, Accessed on 10th March 2020.
- Sengupta, A., Mazumdar, C., Barik, M.S. 2005. E-commerce security—A life cycle approach. Sadhana, 30, 119–140.
- Settle, A., Berthiaume, A. 2020. Debating E-comemrce: Engaging students in current events. Journal of Information Systems Education, 13, 279–286.
- Shahid, S. 2019. https://blog.3dcart.com/ecommerce-security-threats-2019 Accessed on 13th March 2020.
- Sharma, P., Gupta, D., Khanna, A. 2019. e‐Commerce security: Threats, Issues, and Methods. Cyber Security in Parallel and Distributed Computing: Concepts, Techniques, Applications and Case Studies, 61–77.
- Siadati, H., Jafarikhah, S., Jakobsson, M. 2016. Traditional countermeasures to unwanted email. In Understanding social engineering based scams, 51–62. Springer.
- Singh, J. 2014. Review of E-commerce security challenges. International Journal of Innovative Research in Computer and Communication Engineering, 2, 2850–2858.
- Statista, 2018. Online industries most targeted by phishing attacks as of 4th quarter 2019, https://www.statista.com/statistics/266161/websites-most-affected-by-phishing/, Access on 12th March 2020.
- Sumra, I.A., Hasbullah, H.B., AbManan, J.L.B. 2015. Attacks on security goals (confidentiality, integrity, availability) in VANET: a survey. In Vehicular Ad-Hoc Networks for Smart Cities, 51–61. Springer.
- Tang, Q., Linden, L.L., Quarterman, J.S., Whinston, A. 2012. Reputation as public policy for internet security: A field study, Thirty third international conference on information systems, 2–17.
- The SSL Store, 2020. 80 Eye-Opening cyber security statistics for 2019, https://www.thesslstore.com/blog/80-eye-opening-cyber-security-statistics-for-2019/, Accessed on 12th March 2020.
- Thomas, J. 2001. Ethics of hacktivism. Information Security Reading Room, 12. http://www.dvara.net/hk/Ethics-Hacktivism.asp. [Last Accessed: 12th Jan 2021]
- Toapanta, S.M.T., Zamora, M.E.C., Gallegos, L.E.M. 2020. Appropriate security protocols to mitigate the risks in electronic money management. In Smart Trends in Computing and Communications, 65–74. Springer.
- Wang, H., Cao, J., Zhang, Y. 2005. A flexible payment scheme and its role-based access control. IEEE Transactions on knowledge and Data Engineering, 17, 425–436. doi: 10.1109/TKDE.2005.35.
- Wang, J.H., Liao, Y.L., Tsai, T.M., Hung, G. 2006. Technology-based financial frauds in Taiwan: issues and approaches. 2006 IEEE International Conference on Systems, Man and Cybernetics, 2, 1120–1124. IEEE.
- Website Threat Research Report, 2019. An analysis of the latest trends in malware and hacked websites detected, Sucuri. https://sucuri.net/reports/2019-hacked-website-report/, accessed on 10th March 2020.
- Weimann, G. 2004. Cyberterrorism: How real is the threat? 119. United States Institute of Peace.
- Wen, Y., Zhou, C., Ma, J., Liu, K. 2008. Research on E-commerce security issues. International Seminar on Business and Information Management, 1, 186–189. IEEE.
- Wood, S.K. 2016. The role of trust and optimistic bias in public Wi-Fi social engineering, The University of Arizona, 2016, Url: http://hdl.handle.net/10150/613821, accessed on 12th January 2021.
- Xia, H., Brustoloni, J.C. 2005. Hardening web browsers against man-in-the-middle and eavesdropping attacks. 14th international conference on World Wide Web, 489–498.
- Yadav, R., Bhatnagar, S. 2020. Channel collaboration in E-comemrce: A study on channel relationship from the perspective of vendors selling on online platforms, the E-retailers. In Transforming Organizations Through Flexible Systems Management, 223–241. Springer.
- Yang, S., Su, S.Y., Lam, H. 2003. A non-repudiation message transfer protocol for E-comemrce. In EEE International Conference on E-comemrce. CEC 2003. 320–327. IEEE.
- ZDNET, A red ventures company 2020. https://www.zdnet.com/article/wordpress-accounted-for-90-percent-of-all-hacked-cms-sites-in-2018/ Accessed on 14th March 2020.
- Zhiguang, Q.I.N., Xucheng, L.U.O., Rong, G.A.O. 2004. A survey of E-commerce security. Journal of Electronic Science and Technology, 2, 173–176.
- Zhou, Q., Zhang, Z., Wang, Y. 2020. Research on safety management system optimization of B2C E-commerce intelligent logistics information system based on data cube. Journal of Intelligent & Fuzzy Systems, 38, 1585–1592.